hacking padding oracle
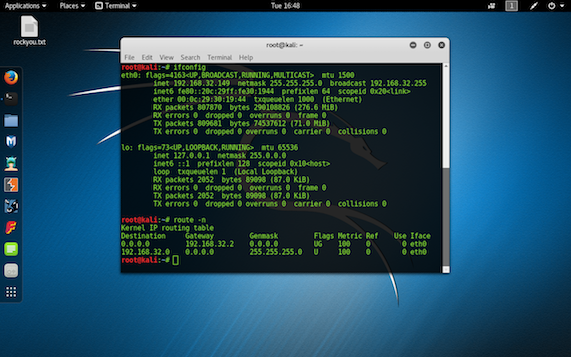
Padding oracle is a vulnerable machine which can be downloaded from "vulnhub.com".The main aim of this machine is to log in as admin. step 1 : Run the "ifconfig" command in terminal in kali linux to know the ip address of the machine from which you will be attcking on the Padding oracle machine.And the "route -n" command will show the default gateway. step 2: Run the "nmap -sV -O -sS -T4 Ip address of gateway/24" command to get the ip address of all the machine that are present on the same network. step 3: After identifying the target ip address run the uniscan command to get the details of all the directories and of all the files. step 4 : copy and paste all the urls in the browser to gather information about the machine.on copying and the pasting the url "http://target ip/login.php". step 5 : On searching the url "http://target ip/index.php" The message directly tells that...





